Netskope Threat Research Labs has discovered a new ATM malware, “ATMJackpot.” The malware seems to have originated from Hong Kong and has a time stamp on the binary as 28th March 2018. It is likely that this malware is still under development. Compared with previously-discovered malware, this malware has a smaller system footprint, a very simple graphical user interface as shown in Figure 1 which displays the hostname along with the service provider information such as cash dispenser, PIN pad, and card reader information.

Figure 1: ATM malware GUI
In ATM “Jackpotting” attacks, the malware is installed on the ATM to dispense large amounts of cash. Jackpotting is on the rise as reported here, and similar attacks discovered in early 2014 targeted ATMs across Europe and Russia as reported here and here. Typically, ATM Malware propagates via physical access to the ATM using USB, and also via the network by downloading the malware on to already-compromised ATM machines using sophisticated techniques. Netskope for Web detects the download of this malware as Gen:Variant.Razy.255528.
Technical Analysis:
The ATMJackpot malware first registers the windows class name ‘WIN’ with a window procedure that is responsible for all of the malware activity as shown in Figure 2
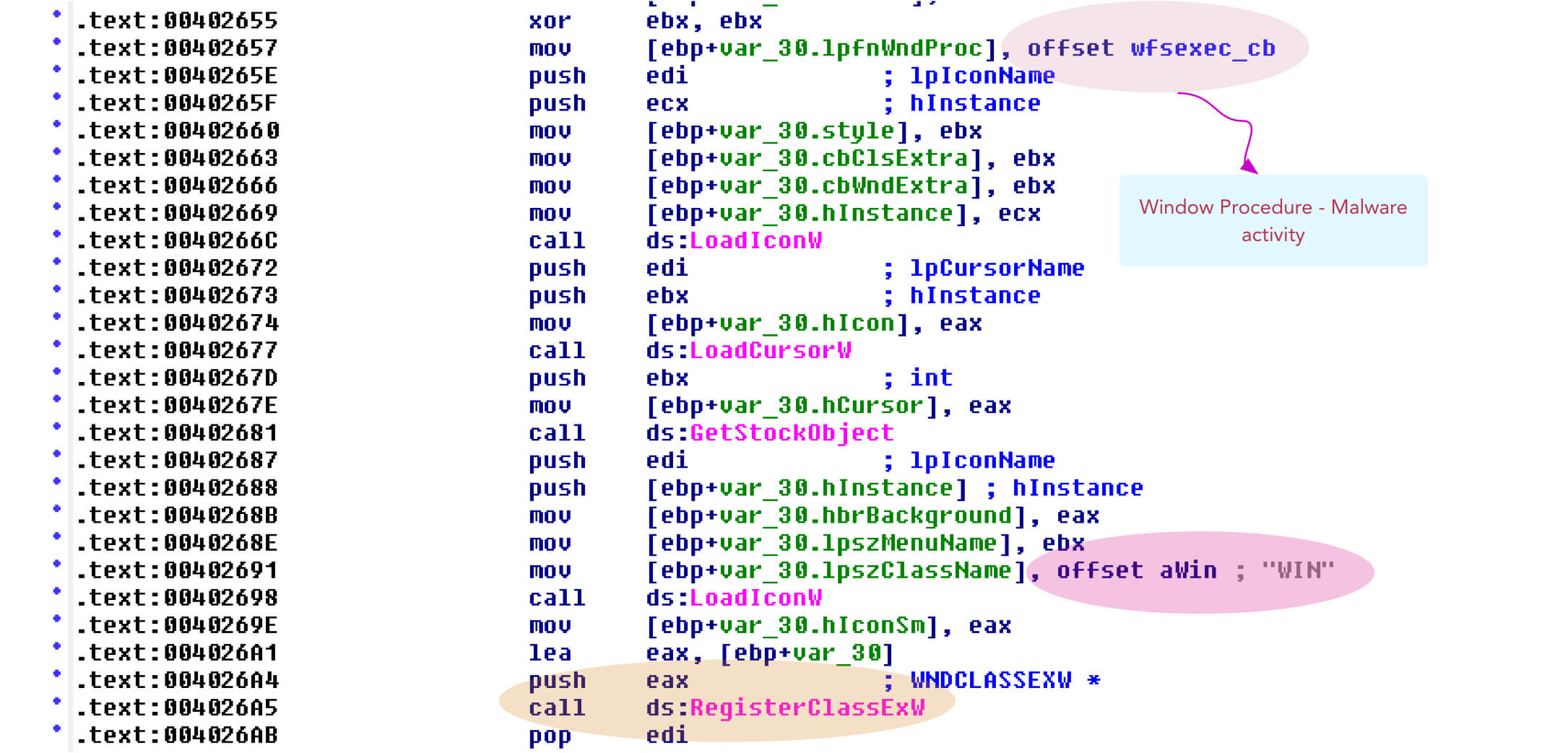
Figure 2: Malware registers window class
After registering a window class, the malware creates the window, populates the options on the window, and initiates the connection with the XFS manager as shown in Figure 3. The GUI of the malware can be seen in Figure 1.
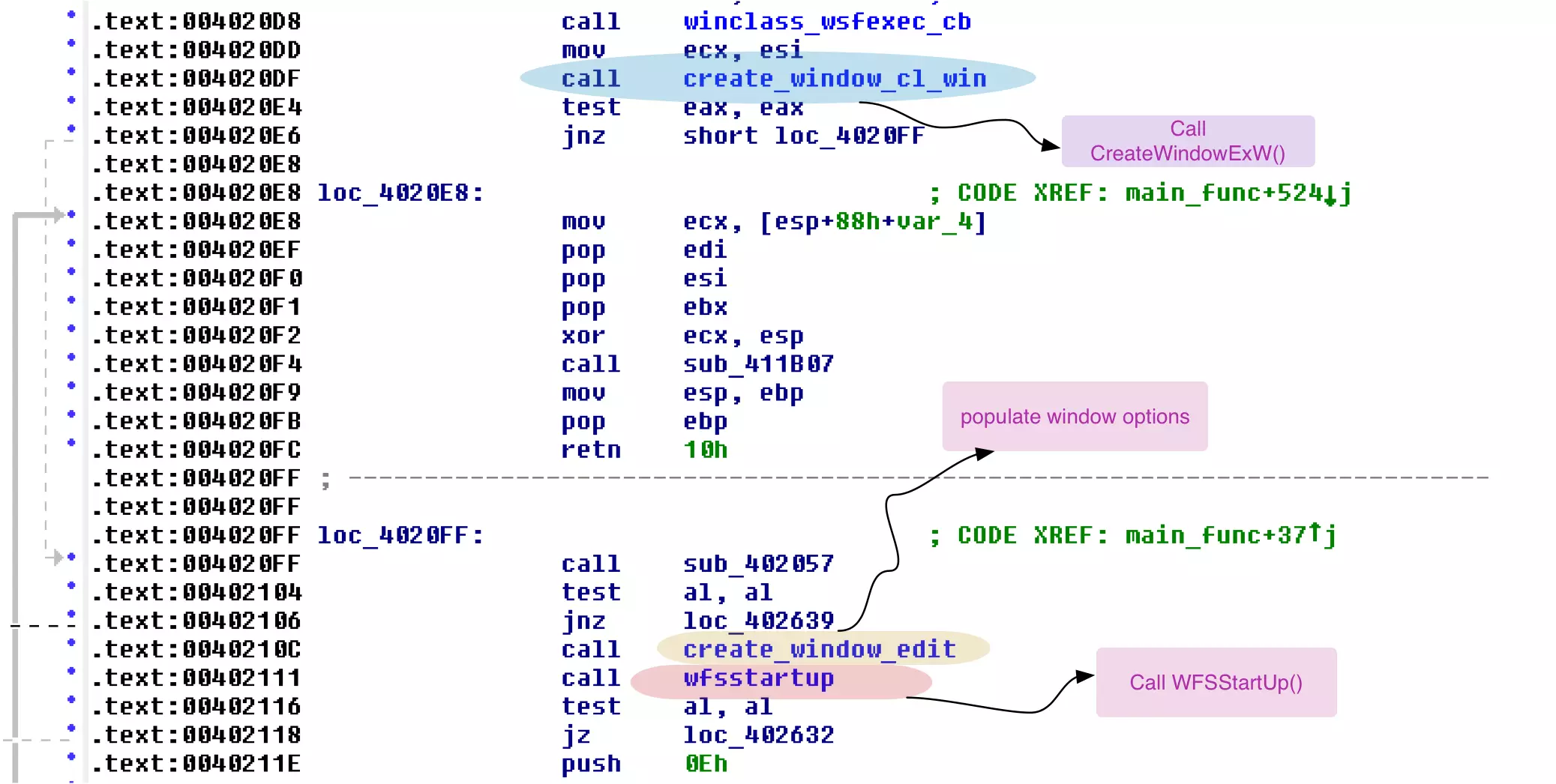
Figure 3: Malware creates window and initiates a connection with the XFS manager
After initiating a connection with the XFS manager, the malware opens the session with the service providers and registers to monitor the events as shown in Figure 4. The malware opens a session with CDM (cash dispenser), IDC (card reader) and PIN (pin pad) service providers.
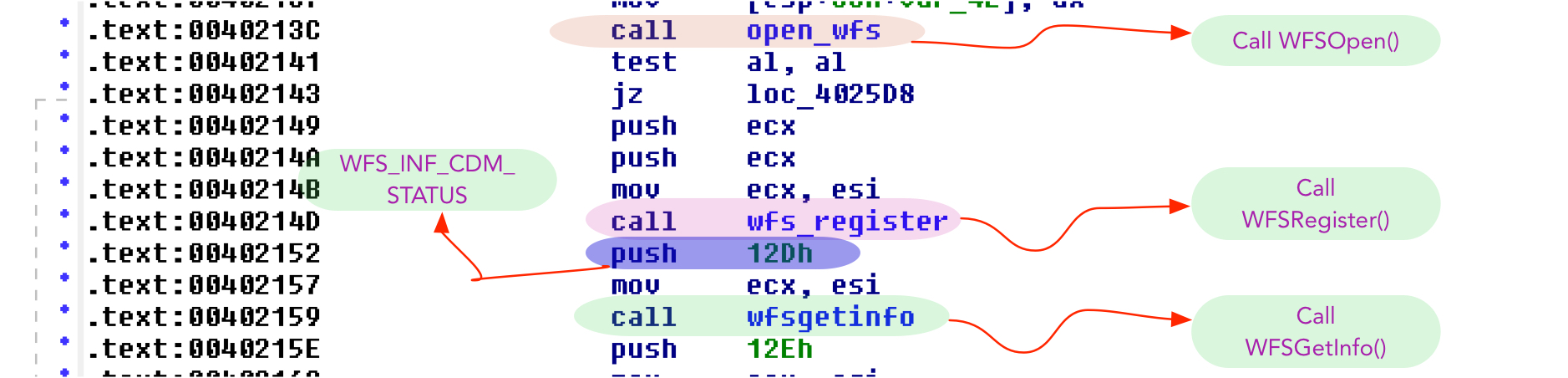
Figure 4: Malware enumerates, open the service providers
After successful registration, the malware can monitor the events from different service providers and execute commands.
Commands:
- Malware reads the data from PIN pad asynchronously using WFSAsyncExecute API call as shown in Figure 5.
- Malware has the functionality to dispense cash as shown in Figure 6.
- Malware also has the functionality to eject the card as shown in Figure 7.
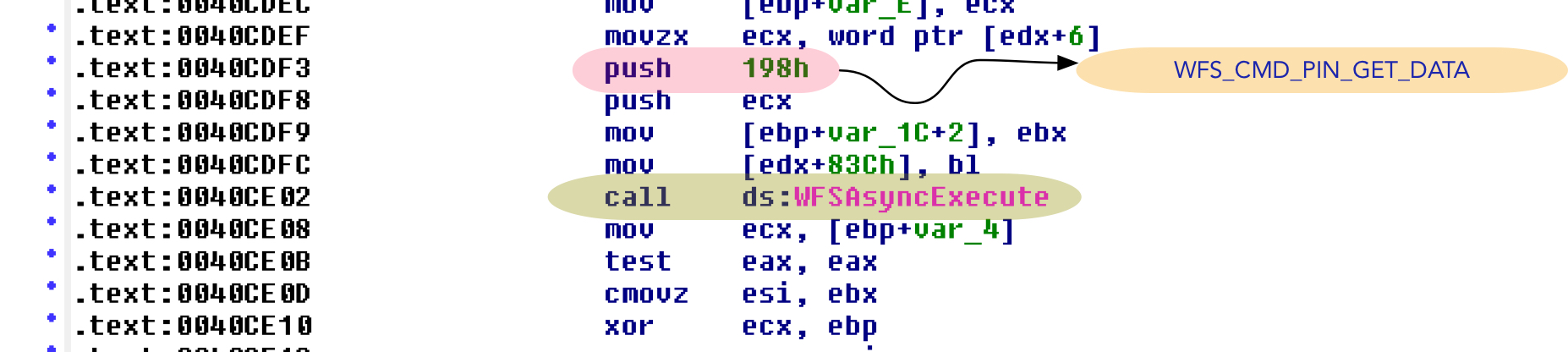
Figure 5: Read data from PIN Pad
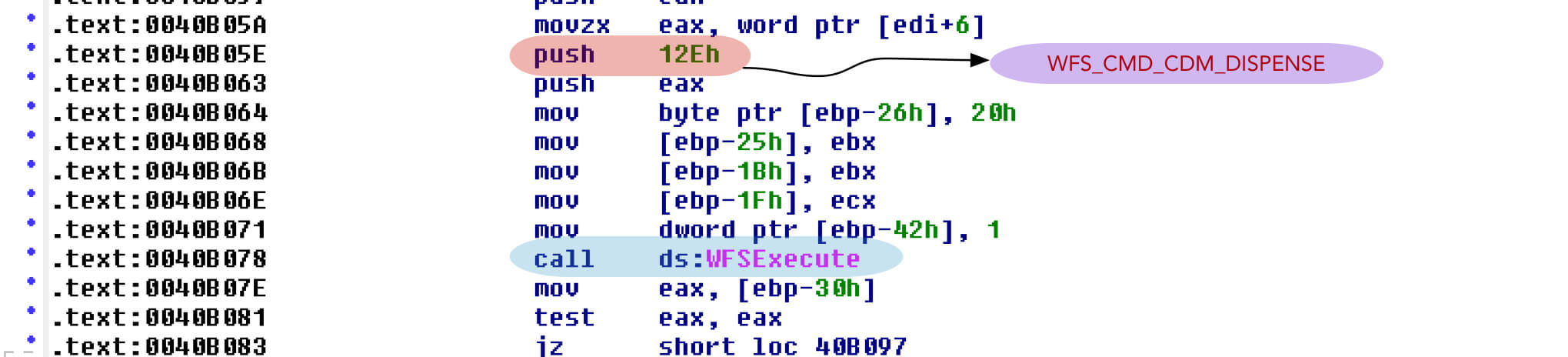
Figure 6: Dispense cash
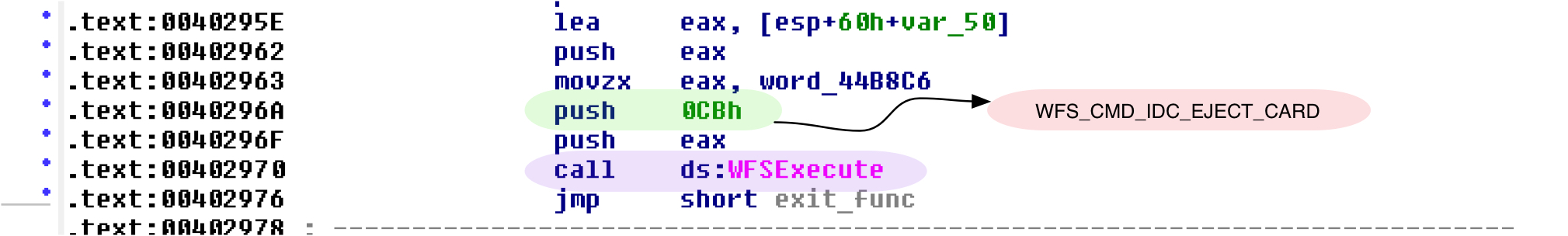
Figure 7: Eject ATM card
The following is the high-level XFS API information seen in the figures above:
WFSStartUp – Initiate a connection between an application and the XFS Manager
WFSOpen – Open a session between an application and a service provider
WFSRegister – Enable monitoring of a class of events by an application
WFSExecute – Send service-specific commands to a service provider
WFSGetInfo – Retrieve service-specific information from a service provider
Additional details on the background of the API’s and other ATM Malware are available here. Netskope Threat Research Labs will continue to monitor ATMJackpot malware and provide updates with additional findings.




 Atrás
Atrás 




















 Lea el blog
Lea el blog